This post is simply a step by step guide to help you set up the Intune Connector for Active Directory (to use its proper name) otherwise known as the AD hybrid join connector for Windows Autopilot. Whatever you’re calling it, it’s the connector that we need to install on one of our servers to act as the go-between to perform the domain join part of a hybrid join when we’re using Autopilot. I was quite surprised when I realised I hadn’t already written this one up so here goes.

This is an image I stole with pride from Michael Niehaus’ post here – https://oofhours.com/2020/06/23/windows-autopilot-user-driven-hybrid-azure-ad-join-over-the-internet-using-a-vpn/
That post talks specifically about the scenario where you are making an Azure Active Directory hybrid-join from any location through a VPN, more specifically it illustrates the capability to generate an offline domain join blob and have the machine complete the domain join at a point when it can see the domain controller.
Either way, you are going to need this connector in place on a server on-premises and the machine account of the server will need to have delegated access to join devices to the domain. More so, they will land in a specific OU that you will create for this process. You can multiple of these if you wish to have some scale or resiliency.
There are no hardware specifications published for the server that hosts this role, it can really be anything. It does need to have clear line of sight to a domain controller (to make the join requests) and it will also need internet access. I’m not aware a formally published list of endpoints that this particular process will use, if I find one I will share. However as it is dealing with Intune it will need the ports and endpoint for that and as it’s using Azure AD it will need those relevant endpoints too. Depending on your desired configuration there may be more, I’ve linked the Microsoft docs page below for your reference.
Windows Autopilot requirements – https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/windows-autopilot-requirements
Setting up the required permissions
Firstly, you need to decide which server(s) will host the connector. Once we have the name of it we need to grant the machine account the relevant permissions to do everything that it needs to.
You’re going to need to be a Domain Administrator to perform this. Also, if you have multiple domains that you wish to perform joins to then you will need to do this in each domain.
- Log onto a DC or perform this remotely through the appropriate tools if you prefer. Then create an organisational unit (OU) into which the devices will be joined. The name is up to you but it will need to match up exactly what is in the Autopilot Deployment Profile. That means, if you decide to rename the OU then expect to see some failures with the connector.
Now right click the OU and select Delegate Control…
- Now select Next
- We need to select Add to go ahead and grant the required server some delegated access
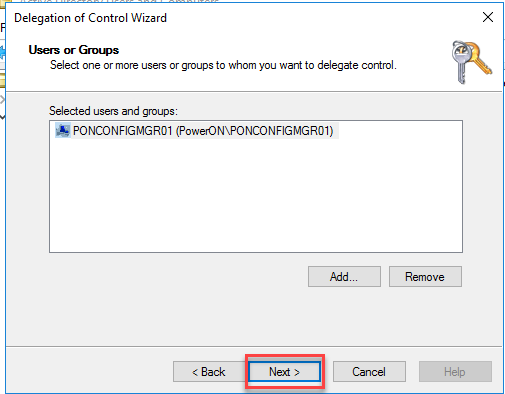
- But first, make sure that you have the “Computers” object type includes

- Now input the server name, select Check Names, click OK.

- That should add the servers machine account into your list of selected users and groups (yes I know, it’s a machine)
Click Next
- Now select the option to Create a custom task to delegate
Click Next

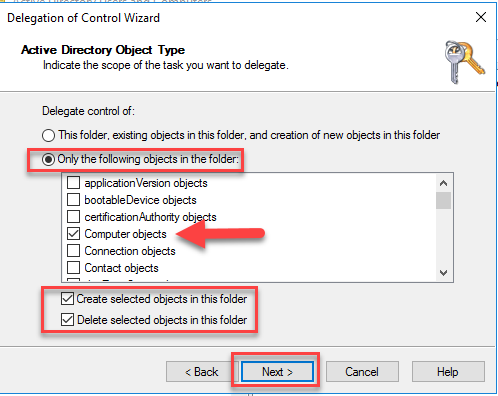
- We now need to ensure the server/connector can only Create and Delete Computer objects in this OU.
Select Only the following objects in the folder
Select computer objects
Select Create selected objects in this folder
Select Delete selected objects in this folder
Click Next
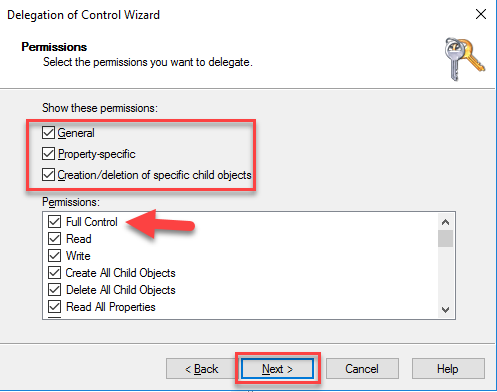
- Now select the specific permissions you wish to delegate.
Choose General, Property-specific, Creation/deletion of specific child objects
Choose Full Control
Click Next
- That’s it, you’ve set all the necessary permissions for that server machine account to perform domain joins.
Next step is to simply install the connector and connect it up to your Intune tenant.
Install the Connector
Installing the connector is relatively simple assuming you have the right network access and permissions. Really it’s a download, install, sign-in approach then you’re done. The steps are here though.
- First, sign into the Microsoft Endpoint Manager admin center (aka.ms/memac)
Now browse to Devices, Enroll Devices.

- Select Intune Connector for Active Directory

- Now click on the add button to add a new connector.
Click the link highlighted which will download the connector setup file for you.

- Move or copy the file to the server which will host your connector. This is the one we granted delegated access to earlier.

- Select to agree to the license terms, if you do indeed agree to them.
Click Install.

- The install should take just a minute or two and once done you can click Configure Now.

- You will now be presented with the connector application, it’s really simple as you can see.
Click Sign In.

- When prompted enter the credentials of an Azure AD user (can be a sync’d user) who has Global Admin or Intune Admin rights.
Prior to June 2020 that user will have required an Intune license, as of June 2020 that’s not required if you don’t want it to be. (go here to set it)
- Once you have authenticated to Azure, you should see a completion.
 If you are not seeing a completion you should check the server has internet access and the user account has the relevant privileges in Azure or Intune.
If you are not seeing a completion you should check the server has internet access and the user account has the relevant privileges in Azure or Intune. - Finally, you’ll need to wait about 10 minutes or so for the connector to appear back in the Admin Center. Back into the enroll devices blade you should see this.

That’s all. Don’t forget to test of course but look out for another post where I walk through that too.
/Peter



Pingback: Intune Connector for Active Directory Service – renew Microsoft Intune ODJ Connector CA cert – 247 TECH
Top Tanks! :-)
LikeLiked by 1 person
Does this allow the Autopiloted machine to be domain joined (in a hybrid scenario) even if not in corporate network and without VPN??
If yes, I guess the first login will need a VPN in any case, correct?
LikeLike
You need the VPN to create a machine based tunnel to complete that hybrid join process, or at the first login the user should initiate the vpn from the login screen prior to login. The machine needs to see the DC at some point prior to the user logging in.
LikeLike
Thank you very much! This helps a lot.
Are computers also added to the domain afterwards if they are already autopilot devices and in use?
LikeLiked by 1 person
Thanks. This joim will only happen during the provisioning process if that’s what you mean. If an existing device is registered into Autopilot and then reset and re-provisioned, the join will happen. Otherwise, no change to an existing device.
LikeLike
Pingback: Powershell Script to Auto Upload and Process Autopilot 4k Hardware Info - Rui Qiu's Blog
Do you have to sync the OU that you created for the intune connector installation back to Azure AD for the Azure AD Hybrid join to complete.
LikeLike
Yes, you will need to sync the AD device across to AzureAD to complete that Hybrid join process.
Mentioned in this article amongst lots of other great info – https://oofhours.com/2020/05/23/digging-into-hybrid-azure-ad-join/
LikeLike
Can I move computers outside of the Intune OU after they are joined?
LikeLike
As long as they’re in an OU which is still syncing to AzureAD then that should be fine.
LikeLike
Hi,
If I am understanding it correctly. I can setup this scenario.
User log in to new laptop and Azure AD join happen. After user login, user connect Azure VPN (DC servers are in Azure) and domain join take place after some time.
Result is Azure AD Hybrid join device, am I right?
LikeLike
Almost. The device joins AzureAD during the Autopilot process (later converted to a HAADJ), them submits an AD join request via this connector. The VPN MUST come up before the user logs in, else there will be nothing to authenticate the login (as it’s authenticating to a DC). Typically that would be a VPN with a machine tunnel that can authenticate without user interaction, or the user makes the connection from the login screen before authenticating. You might need certificates to do that authentication.
The hybrid joined device is almost the same as an on-prem device so you have to keep that in mind.
LikeLike
I have went through the steps. Thanks for the guide. I have a query setup on a custom name group “(device.devicePhysicalIDs -any _ -contains “[ZTDId]”)” to pull in the autopilot devices. However, im not seeing those systems syncing down to the on-prem DC. Am I missing something?
LikeLike
After the Parameter -Any You need a bracket:
(device.devicePhysicalIDs -any (_ -contains “[ZTDId]”))
LikeLike
Pingback: Getting started with Microsoft Intune – 3six5
Pingback: How to setup Microsoft Intune – Day 1. – Move2Modern – Andy Jones