Whilst testing out the new features of Configuration Manager 1906, I enabled the new Azure Active Directory Group Discovery and also the collection synchronisation to Azure AD. More info here – https://morethanpatches.com/2019/08/16/configuration-manager-1906-cloud-attached-management/
Unfortunately, (in my lab environment) I fell foul of a bug within this feature which is related to Azure AD app registration permissions.
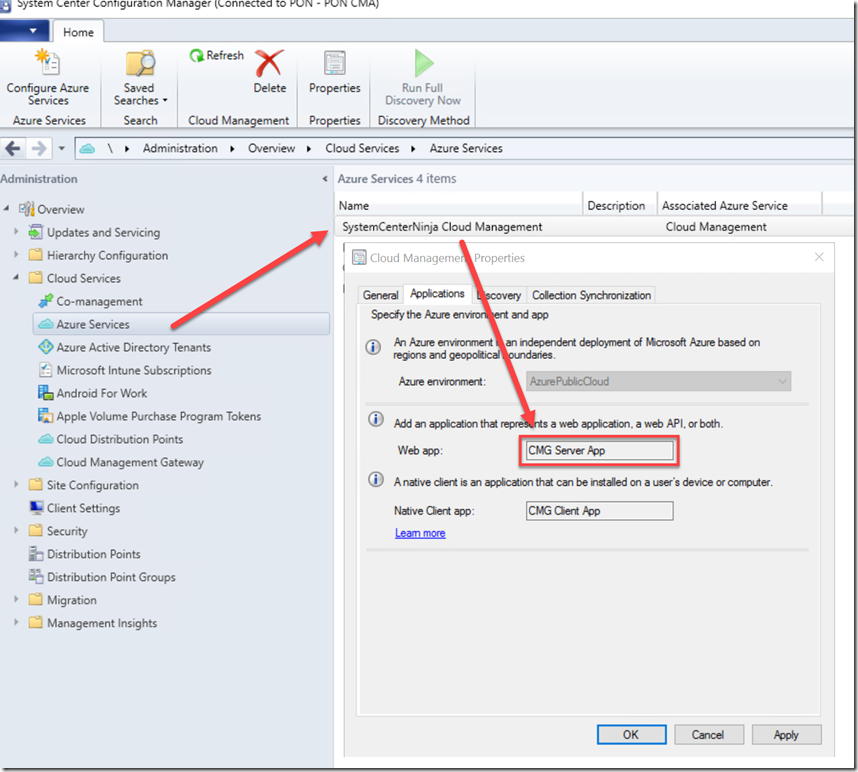
When you select the Azure AD Service, there will be a corresponding Web App in Microsoft Azure which allows the two systems to talk to each other.
Administration > Cloud Services > Azure Services > [MyAzureService} > Applications > Web app
As this was my lab I skimmed through the docs and got a little click eager. That said, it’s not evident there is any change required as the docs haven’t been fully updated on this yet. I’m assured they will though.
In my environment the Web app was existing as it’s been used in previous versions. From ConfigMgr 1902 there was a change towards using Microsoft Graph for communicating with such features. In 1906 the AAD Group discovery and collection sync to AAD utilise Microsoft Graph too, however it doesn’t update the permissions on your web app for you. After 1902 you would need to change your web app permissions to allow Microsoft Graph to read your AAD. If you’re creating this from new in 1902 onwards then you won’t notice any difference as the wizard will set the appropriate permissions for you.
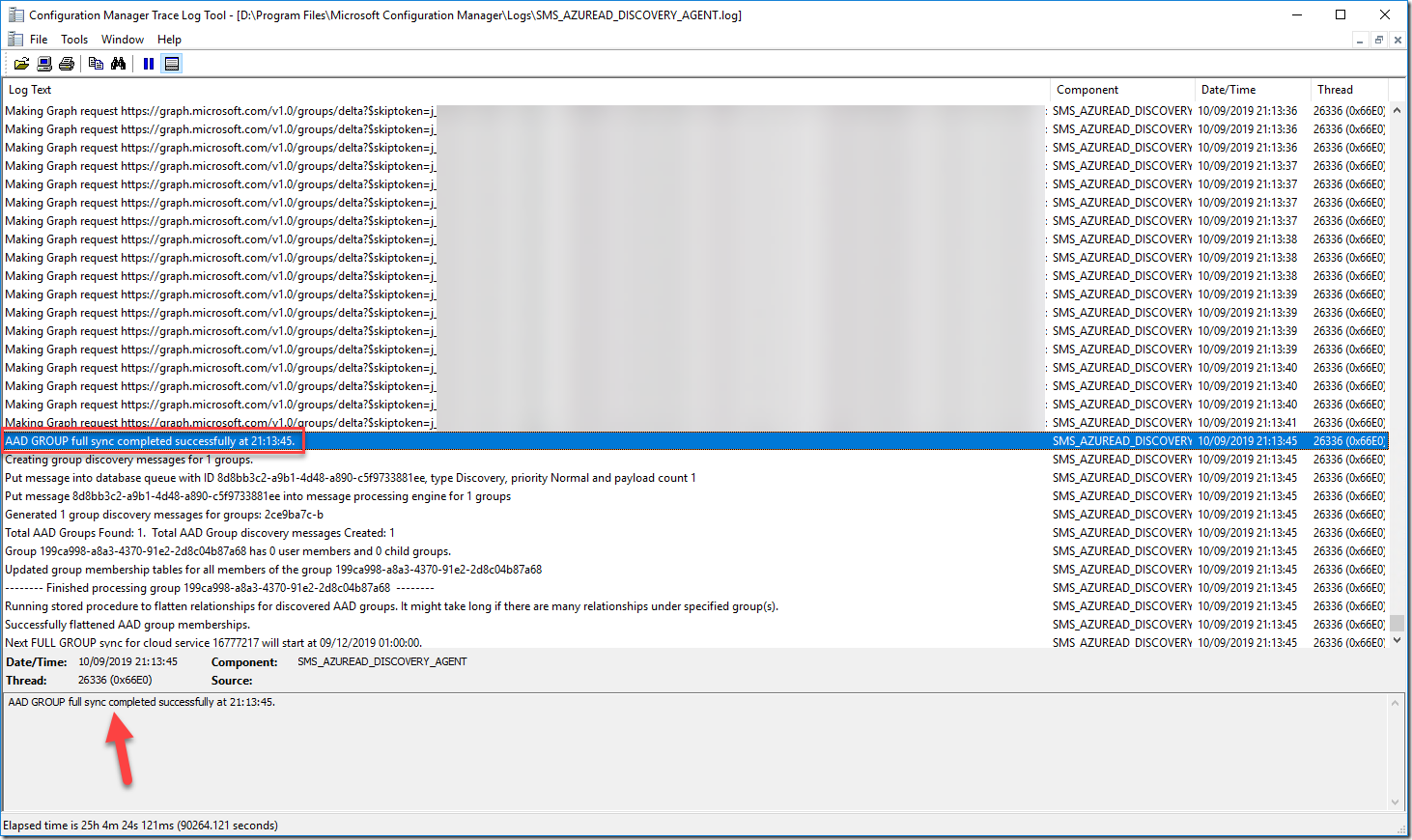
Usually this would be a minor pain if you hadn’t changed it, you’d probably see an error and you would figure it out eventually. However in this instance I fell into a bug which drops the feature into an infinite code loop and as a result my SMS_AZUREAD_DISCOVERY_AGENT.log file got a little crazy and filled very very quickly. It was logging multiple lines every second with a “Forbidden” error and status code.
I contacted the product group on this one and got a prompt response which quickly led me to a resolution.
To stop this
If you fall into this, you need to disable the AAD discovery and any collection to AAD sync, then restart the SMSEXEC service on your Configuration Manager site server.
To fix this
You essentially need to change the permissions on the Web app in Azure.
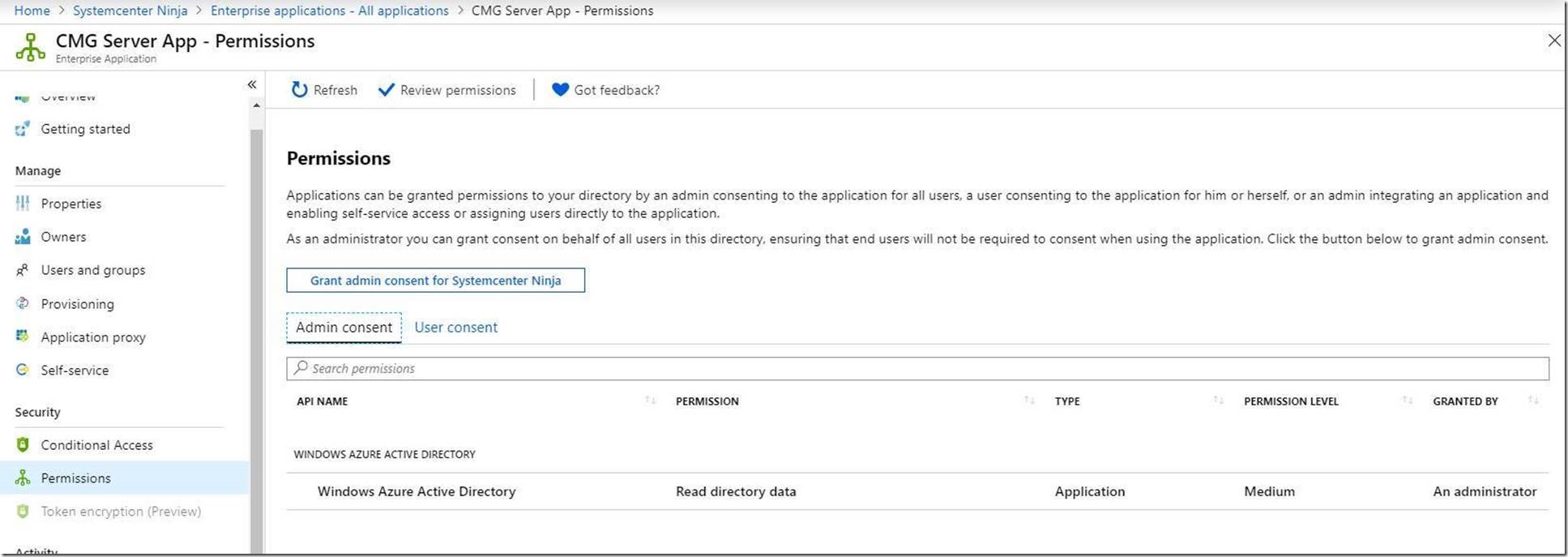
In the Azure portal browse to Azure Active Directory > Enterprise Applications > [MyAzureService] > Permissions
My ‘old’ permissions were this:
I needed to add some permissions for Microsoft Graph, like so:
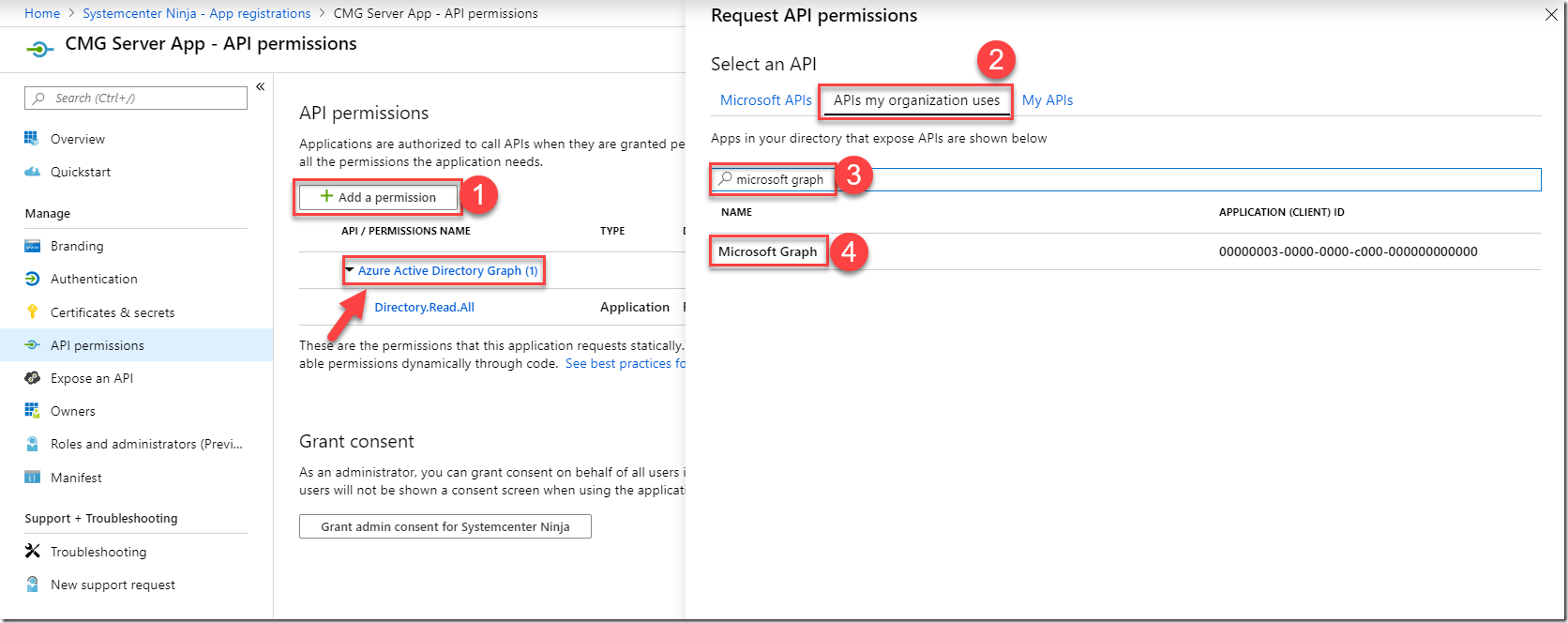
If you’re not sure how to do this, go to the Microsoft Azure Portal > Azure Active Directory > App Registrations
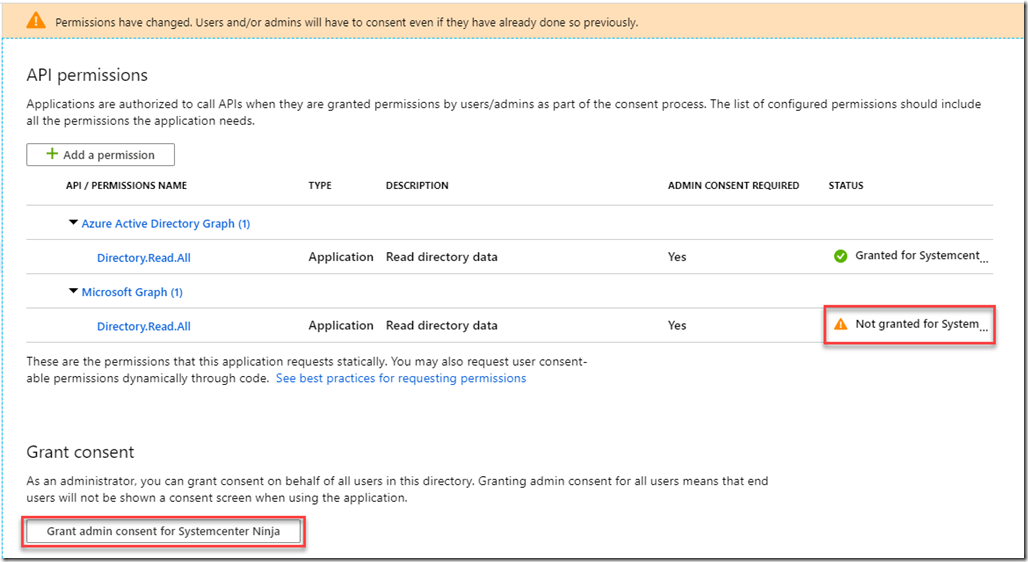
Now choose the relevant app registration (the one shown as web app in ConfigMgr) and go to the API permissions. Note in the screenshot that although Graph has permissions to my app registration, that is Azure Active Directory Graph, we want Microsoft Graph. There’s a difference.
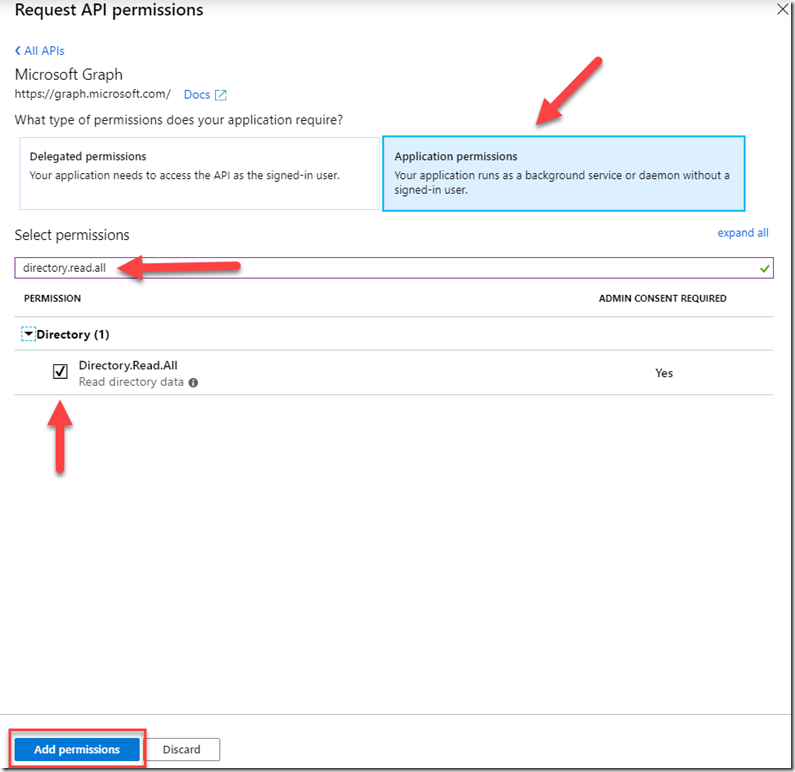
Choose Application permissions, then filter on Directory.Read.All and tick the box for that permission. Now Select Add permissions.
Note that I now have a warning. This means that although I have set the permissions, I need to grant consent for the app to do whatever permission I have set. So now I need to hit the Grant admin consent for <Your Org> button.
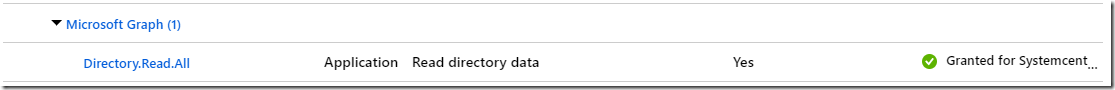
Once this is done, we should see a green tick instead of the warning.
A little side note, I did this manually in the Azure portal, if for some reason you need to do this multiple times or prefer to use PowerShell then you can use this guide from Martin Ehrnst as a reference for modifying the API permissions.
https://adatum.no/azure/azure-ad-application-using-powershell
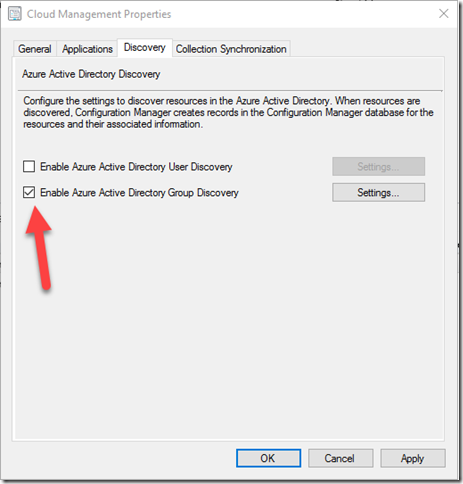
That should be all the permissions done. Now to jump back into ConfigMgr and set the Azure Active Directory Group Discovery again. So back into Administration > Cloud Services > Azure Services and select the Azure service then go to the properties.
Switch to the Discovery tab and enable Azure Active Directory Group Discovery.
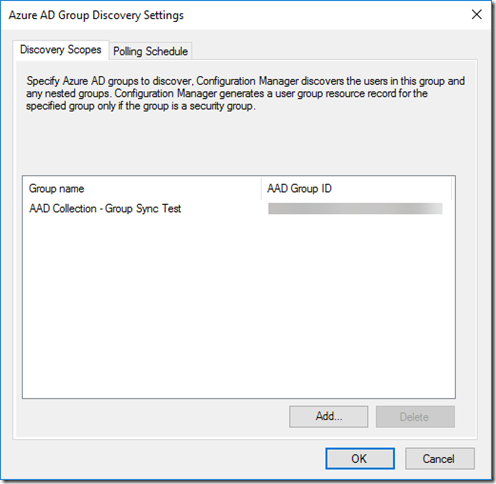
Make sure you have an Azure Active Directory Group set to synchronise…
Now we can OK twice to apply the change.
If we now go back and visit the SMS_AZUREAD_DISCOVERY_AGENT.log file we should see the attempt again to perform an Azure Active Directory Group synchronisation and hopefully this time with some better success.
That’s all, enjoy the group sync feature and let me know how you get on.
/Peter


![clip_image002[5] clip_image002[5]](https://itbyme.files.wordpress.com/2019/09/clip_image0025_thumb.jpg?w=1798&h=405)

Great Stuff Peter as always. Some other reports of 1906 Known issues https://www.anoopcnair.com/sccm-1906-known-issues-fixes/
LikeLiked by 1 person
Pingback: SCCM 1906 Known Issues - List of Fixes
Had same problem, but a update the application setting resolved the problem (in sccm console – \Administration\Overview\Cloud Services\Azure Active Directory Tenants)
LikeLike