Not the snappiest title, I’ll work on it. But for now I will share the info anyway. I was asked about storing BitLocker recovery keys into Azure Active Directory with Microsoft Intune, which natively is fairly straight forward for Windows 10 fixed or operating system drives but no so much for removable drives. I’ll be clear here, there isn’t a seamless solution for this right now, but I believe there will be at some point. With that in mind this is workaround but it does work.
As the saying goes – we can take our horse (removable drive) to water (Windows) but we can’t force it to drink (encrypt). In other words you can set the policy in Intune or other MDM to make Windows prompt for encryption of removable drives but we can’t force the encryption or indeed control/mandate the storage of the recovery key. These are the options available right now:
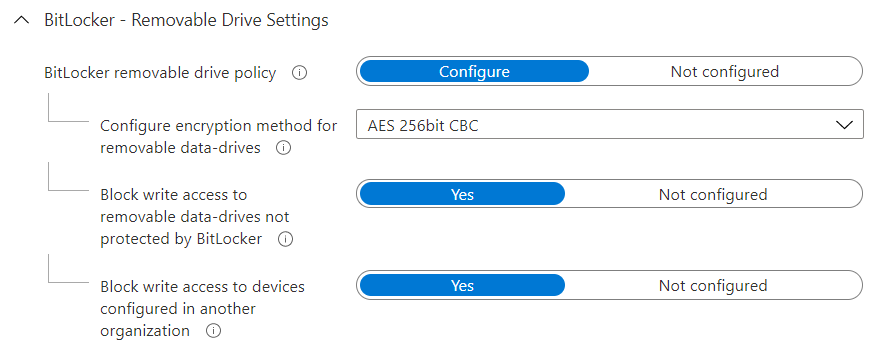
Of course, with any workaround there has to be a catch or some effort required. Well here’s two.
Catch #1
The first catch is, we need to have the user store the recovery key somewhere beforehand in order to encrypt the key. This can be as a file or printed. There is likely a way to capture this from the get go but I haven’t worked on that yet.
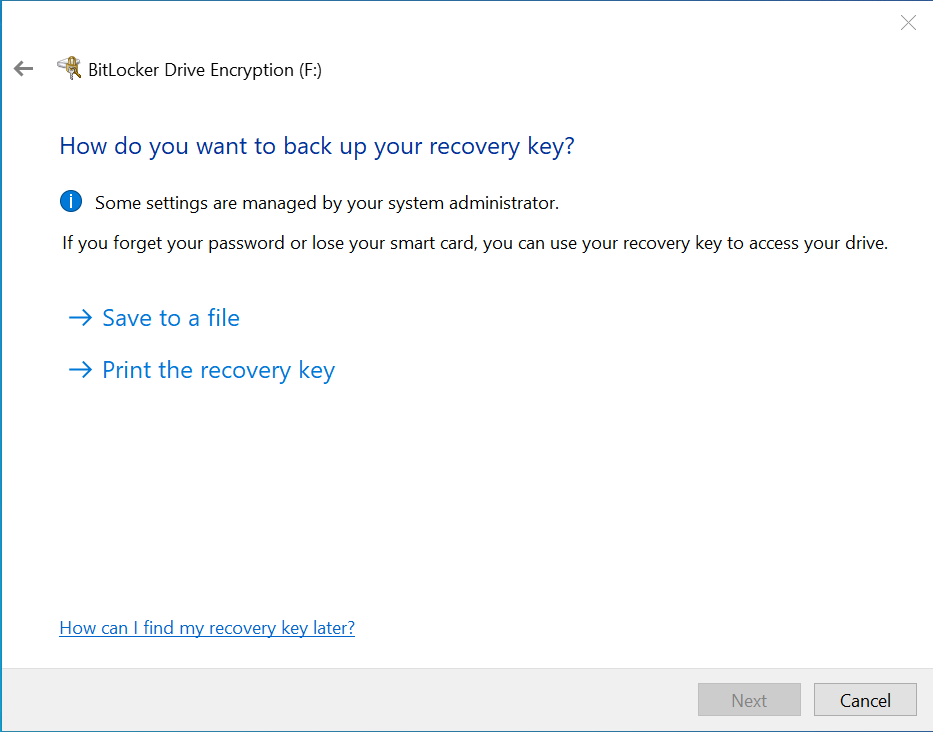
Catch #2
The second catch here is that if you choose to store the recovery key as a file, this must be stored on an unencrypted volume. The chances are that if you’re doing removable drive encryption then you’re also doing OS or fixed drive encryption so that kinda rules that option out, especially if you’re mandating in your policy to block write access to drives that aren’t already protected by BitLocker.
The tip here is to print it to a PDF printer that then saves the key as a PDF file in whatever location you want.
The workaround
So, if you’re still reading then we have an option after those catches are covered or acknowledged. We can run a fairly simple command to push the removable drive recovery keys up into Azure Active Directory where they are associated with the device they are connected to. Of course, that is on the assumption that the device is Hybrid Azure AD joined or Azure AD joined.

We can run the following PowerShell command to do this:
#Detect the Removable Drive letters #Taken from https://stackoverflow.com/questions/10634396/get-the-drive-letter-of-usb-drive-in-powershell $RemDrive = gwmi win32_diskdrive | ?{$_.interfacetype -eq "USB"} | %{gwmi -Query "ASSOCIATORS OF {Win32_DiskDrive.DeviceID=`"$($_.DeviceID.replace('\','\\'))`"} WHERE AssocClass = Win32_DiskDriveToDiskPartition"} | %{gwmi -Query "ASSOCIATORS OF {Win32_DiskPartition.DeviceID=`"$($_.DeviceID)`"} WHERE AssocClass = Win32_LogicalDiskToPartition"} | %{$_.deviceid} #Store the recovery key to AzureAD with the device record #Based on https://docs.microsoft.com/en-us/powershell/module/bitlocker/backup-bitlockerkeyprotector?view=windowsserver2019-ps $BLV = Get-BitLockerVolume -MountPoint $RemDrive BackupToAAD-BitLockerKeyProtector -MountPoint $RemDrive -KeyProtectorId $BLV.KeyProtector[1].KeyProtectorId
I haven’t needed to expand this yet, but it could be modified to include a loop for multiple drive letters. The $RemDrive variable will return multiple drive letters if there is more than one – that I have tested. Also, each time the recovery key is changed, that will also be seen as new and uploaded as such.
I haven’t developed this idea any further at this stage as I’m fairly confident this will natively arrive into Intune and AzureAD at some point. However, use cases with these couple of lines of script could include a scheduled task on the device (triggered by device insert event maybe), a PowerShell UI to walk through this from drive insertion, Intune PowerShell script and also maybe using it in some way with a proactive remediation in Endpoint Analytics. If there’s demand, I might build it out but at the moment I’ll hold out on this appearing natively.
Hopefully that’s useful to someone. Enjoy.
/Peter
Is there a way to automate this to upload to Azure AD on protection of the removable drive / setting of the password?
LikeLike
I haven’t built it out further but I think you could do something to detect an event then trigger that script. I seem to recall there was an event ID that signified the encryption was done.
LikeLike
It is certainly possible to use your script combined with a Scheduled Task.
The Scheduled Task will start after EventID 24667 (the moment when the BitLocker encryption of the USB device is finished).
It works like a charm, we now use it in our company. :-)
LikeLiked by 2 people
What context do you run the script under. Also, Any particular reason you wait until encryption is complete, and don’t backup as soon as encryption starts (event ID 24660)
LikeLike
Hi, we run the script under “system”.
No specific reason not to store the BitLocker key at the start (EventID 24660).
If you prefer EventID 24660, please make the tiny adjustment in the script. :-)
LikeLiked by 1 person
Any error checking possible here? I’d like to know if there was an error storing the Bitlocker key before my user threw away their PDF file.
LikeLike